Applicable Products
- Citrix Workspace App
- Receiver for Windows
How to Configure Citrix Receiver for Windows to Manually Add HTTP Stores. How to configure Receiver to not use proxy settings set up on IE. Self-Service Mode - By adding a StoreFront account to Citrix Workspace app or configuring Citrix Workspace app to point to a StoreFront website, you can configure self-service mode, which allows you to subscribe to applications from the Citrix Workspace app user interface. This enhanced user experience is similar to that of a mobile app store. First you need to ingest both the citrixbase.admx and the receiver.admx - you can do these both, and the OMA-URI configuration items, in a single Device Configuration Profile. The CitrixBase ADMX you can copy/paste straight in, but crucially before you copy/paste in the contents of receiver.admx you need to remove the 'ica-file-signing' section.
Objective
Click Stores on the left. On the right, click Enable Remote Access. Select No VPN tunnel. Note: if you want Receiver to automatically launch a VPN tunnel, then see CTX200664 How to Configure Receiver for Seamless Experience Through NetScaler Gateway. 💡; Check the box next to the NetScaler Gateway object you just created and then click OK.
Citrix Workspace app is the new universal app for all workspace services, that will encompass all Citrix clients and app capabilities over time.
This article describes how to install Citrix Receiver for Windows and configure Single Sign-on authentication to XenApp/XenDesktop. After configuring Single Sign-on, users can log onto Citrix Receiver for Windows and launch XenApp/XenDesktop sessions without having to enter their credentials multiple times.
Note: StoreFront 3.11 and later enable Citrix Receiver Launcher for RfWeb when accessed using Microsoft Edge. This enables client detection and upgrade as well as Domain pass-through authentication.
Instructions
Single Sign-on authentication can be configured on both new and upgraded setup.
| Configuring Single Sign-on on a new Citrix Receiver for Windows setup |
| Configuring Single Sign-on on an upgraded Citrix Receiver for Windows setup |
| Single Sign-on Troubleshooting and Diagnostics |
To configure Single Sign-on on a new setup:
1. Enable User name and password and Domain pass-through on StoreFront or the Web Interface
Depending on the XenApp/XenDesktop deployment, Single Sign-on authentication can be configured on StoreFront or the Web Interface using the Management Console.
StoreFront server: Launch StoreFront Studio, go to Store > Manage Authentication methods > enable Domain pass-through.
Note: Single Sign-on is not supported if Citrix Receiver for Windows is connected to XenApp/XenDesktop using NetScaler Gateway.
| Scenario | Steps | Description |
|---|---|---|
| Configured on StoreFront or the Web Interface with Management Console | StoreFront server: Launch StoreFront Studio, go to Store > Manage Authentication methods > enable Domain pass-through. | When Citrix Receiver for Windows is not configured with Single Sign-on, it automatically switches the authentication method from Domain pass-through to Username and Password, if available. |
| Receiver for Web IS Required | Launch Stores > Receiver for Websites > Manage Authentication methods > enable Domain pass-through. | When Citrix Receiver for Web is not configured to allow Domain pass-through, it automatically switches the authentication method to Username and Password, if available. If you are launching published applications using web browsers for Storeweb, enable the Single Sign-on feature as described in the sectionGroup Policy Settings. |
| StoreFront IS NOT configured | If Web Interface is configured on a XenApp server, open XenApp Services Sites > Authentication Methods > enable Pass-through. | When Citrix Receiver for Windows is not configured with Single Sign-on, it automatically switches the authentication method from Pass-through to Explicit, if available. |
2. Configure XML trust services on the Delivery Controller
On XenDesktop 7 or later or XenApp 7.5 or later, run the following PowerShell command as an administrator on the Delivery Controller:
asnp Citrix*
Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $True

Refer to the Knowledge Center article: Error: 'An error occurred while making the requested connection'.
Note: On XenApp 6.5, XML Service Port and Trust is enabled using the Graphical User Interface. For more information, see Configuring the Citrix XML Service Port and Trust.
3. Modify Web Browsers settings and Install Citrix Receiver for Windows with Single Sign-on
3.1 Modify the web browsers settings
3.1.1 Configuring IE, Chrome, Edge browsers and Citrix Workspace for Windows for Single Sign-on
Modify the Internet Explorer settings to add StoreFront URL or Web Interface URL to the list of Security Zones in Internet Options. There are two methods to modify Security Zones:
NOTE: At any time, use only one of the following methods.

| Option 1 |
|---|
|
| Option 2 |
|---|
Note: Automatic logon with current user name and password can be configured using Group Policy. For more details, see Managing Browser Settings with Group Policy Tools. |
3.1.2 Configuring Firefox for Single Sign-on
- Open Firefox
- Type about:config in the address bar
- A security warning page will appear. To continue, click “I accept the risk!”
- List of configurations will be available. In the search bar type “network.automatic-ntlm-auth.trusted-uris” and add the store URL to that configuration
3.2 Install Citrix Receiver for Windows
- Download Citrix Receiver for Windows (CitrixReceiver.exe) from Citrix Downloads.
- Log onto the client device with administrator privilege.
- You can install Citrix Receiver for Windows in two ways:
Using the Graphical User Interface Using the Command Line Interface - Double-click CitrixReceiver.exe.
- In the Citrix Receiver Installation wizard, select Enable Single Sign-on.
- Click Next.
- After the installation is complete, log off from the client device and log on again.
- Open a command prompt as an administrator and change to the directory to where CitrixReceiver.exe is located.
- Run the following command to install Citrix Receiver for Windows with the Single Sign-on feature enabled:
CitrixReceiver.exe /includeSSON /silent
- After the installation is complete, log off from the client machine and log on again.
- Launch the Task Manager to verify that the ssonsvr.exe process is running.
Users should now be able to log on to an existing Store (or configure a new Store) using Citrix Receiver for Windows without providing credentials.
Group policy settings
Configuration described in this section is required in two cases:
• When access to StoreWeb using web browsers is required.
• Citrix Receiver for Windows version 4.3 or earlier is used.
For newer versions of Receiver (4.4 onwards) that do not require SSON via web browsers, the configuration is optional
Using Citrix Receiver for Windows Group Policy template files
• Add Citrix Receiver for Windows template files to the Local Group Policy Editor. For more information, see Configure Receiver with the Group Policy Object template . Be sure to use the ADM template of the same version as the Receiver on the Client.Follow the below steps to configure the policy
1. Open Local Group Policy Editor. Navigate to Citrix Receiver > User authentication.
Navigate to Citrix Receiver > User authentication.2. Open the Local user name password policy.
3. Select Enable pass-through authentication.
4. Click Apply and OK.
Note: If the existing version of Citrix Receiver for Windows does not have the Single Sign-on component installed, upgrading to the latest version with the /includeSSON switch is not supported.
After the installation is complete, log off from the client device and log on again.
Single Sign-on Diagnostics
In Citrix Receiver for Windows Version 4.5, you can use Configuration Checker to diagnose the Single Sign-on configuration.
Right-click the Citrix Receiver icon in the notification area and select Advanced Preferences > Configuration Checker.
The Configuration Checker window appears.Select SSONChecker and click Run.
The test runs on all the SSON checkpoints.
After the test is complete, the results are displayed for each test.
The test describes if all the configuration requirements for Single Sign-on are met.
For more information, see Using Configuration Checker to validate Single Sign-on configuration
Verify the list of Network Providers
If users face any issues with Single Sign-on, Citrix recommends that you verify the list of network providers list on the client machin e as described below:
Click Start.
Enter View network connections. The Network Connection window appears.
Press ALT to display the menu. Click Advanced > Advanced Settings
Advanced Settings window appears.Click the Provider Order tab.
Move “Citrix Single Sign On” to the top of the list to change the order of network providers.
Additional Resources
Adding Citrix resources to the Start Menu and Desktop has been possible for quite some time now with the use of Citrix Receiver. The most recent version 4.5 of Receiver for Windows allows users to select the Start Menu and Desktop location themselves. You can also configure the location via GPO and command line install which I will show.
The best experience for users using Receiver includes single sign-on and resources residing in a specific folder within the Start Menu and/or Desktop.
To configure single sign-on with Receiver for Windows see https://www.jgspiers.com/citrix-sso-receiver-and-receiver-for-web/
To install Receiver via command line see https://www.jgspiers.com/command-line-install-citrix-receiver-for-windows/
Let’s take the following scenario and implement it:
Users should have Citrix Receiver with single sign-on configured and the Citrix store must be automatically provisioned for the user. Applications should reside within the Start Menu and optionally on the Desktop. Some applications must automatically appear in the Start Menu whilst other applications should only appear if subscribed by the user using Self Service. Applications must also be categorised within their own folders.
Let’s begin.
Step 1 – Configure Group Policy for single sign-on and StoreFront provisioning
If you haven’t already imported the Receiver.axmx file into the PolicyDefinitions folder within SYSVOL on your Domain Controller do so now. Receiver policy templates can be downloaded from Citrix. An ADML file will also be downloaded and must go within the language folder in PolicyDefinitions such as en-US.
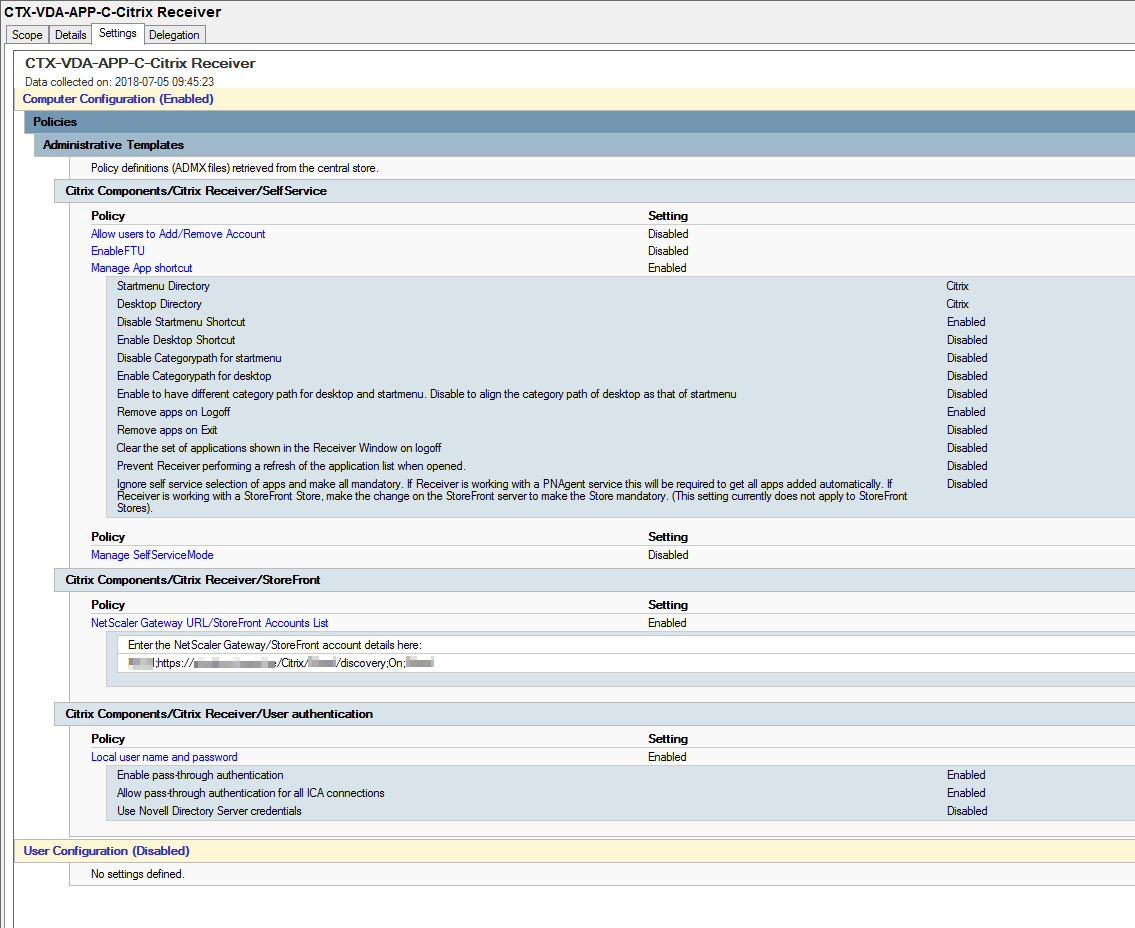
Now create or edit an existing Group Policy object. Navigate to Computer Configuration -> Policies -> Administrative Templates -> Citrix Components -> Citrix Receiver -> User Authentication -> Local user name and password.Tick Enable pass-through authentication and Allow pass-through authentication for all ICA connections. Click OK.Navigate to Computer Configuration -> Policies -> Administrative Templates -> Citrix Receiver -> Storefront -> Storefront Accounts List.
Check Enabled and click Show…Enter a store name as below. The XenApp value at the beginning matches the same name as my Citrix store so this value should match yours. The On value makes the store active within Citrix Receiver. I am using HTTP for my store and whilst this is not the recommended protocol I want to use it to show you a couple of things you must do in the event your store also uses HTTP. Click OK.Step 2 – Install Receiver via command line installing the SSON component and configure Start Menu integration
Simply run a command line install such as the one below. ALLOWADDSTORE=A allows HTTP stores to be added to Receiver (by default this is not allowed). STARTMENUDIR is used to specify the folder that applications will fall under within the Start Menu. In this case, My Citrix Apps. More command line strings can be used and more detail on what is available can be found here https://www.jgspiers.com/command-line-install-citrix-receiver-for-windows/After the Receiver install and at least a log off/on for the SSONSVR.EXE service to kick in you should see your configured store as below. Unfortunately by default this message appears. This is because the store is HTTP. This takes us to step 3. Step 3 – Edit the Registry to optimise delivery of applications to Start Menu/Desktop and fix HTTP error
To get around the Your apps are not available at this time message add a REG_SZ entry with the name ConnectionSecurityMode and the value Any.. Remember that this is only needed for HTTP stores. This REG_SZ value should be created in:
HKLMSoftwareCitrixAuthManager – 32bit machines.
HKLMSoftwareWOW6432NodeAuthManager – 64bit machines.Next to speed up the Self Service application refresh (the time it takes resources to appear in the Start Menu or Desktop) we can create another two REG_SZ values. The names are as below both with a value of 1. Create these in:
HKLM/Software/Citrix/Dazzle – 32bit machines.
HKLM/Software/WOW6432Node/Citrix/Dazzle – 64bit machines.Step 4 – Testing it all works and categorising applications
Launch Receiver. You should be autenticated by SSO. Subscribe to an application.Now look how the application appears in the Start Menu under the My Citrix Apps folder. A requirement was to place applications within their own folders for better organisation. Navigate to Citrix Studio, edit the properties of the application, click Delivery and enter a name under Application category (optional). Now click OK.
Note: You can use the Add shortcut to user’s desktop check-box to add this application to the users desktop. Another requirement was to make an application automatically appear within the Start Menu and Desktop folders without the user having to manually subscribe. To do this, edit an applications properties. We will first specify RDP under the application category. Now click on Indentification and enter KEYWORDS: Mandatory beneath Descriptions and keywords. Doing this subscribes the application to users and they cannot remove the subscription. We could have also used the Auto keyword and with this keyword users can unsubscribe. Click OK.The next time you launch Receiver the RDP mandatory application appears. Now look at the Start Menu. Applications are under their own folder as specified within Studio and RDP now also appears. Remove Microsoft Outlook by right-clicking and removing within Receiver. The application also dissapears from the Start Menu.
Try removing the mandatory application. You can’t.As I mentioned users now have the ability to configure application shortcuts using Receiver for Windows 4.5. Right-click the Receiver icon and click Advanced Preferences.Click Settings Option.Notice the options available. Specify a Start Menu Folder and click OK.Click Yes.Now applications appear in the Override Folder. Specify a folder name for Desktop. Click OK.After Receiver starts the folder is created on your Desktop and populated with subscribed applications. Here’s a closer look showing the RDP folder. From my testing user specified locations using Receiver 4.5 overrides anything set via CMD Receiver install or GPO. To configure Desktop and Start Menu shortcuts via GPO edit or create a new GPO. Navigate to Computer Configuration -> Policies -> Administrative Templates -> Citrix Receiver -> SelfService -> Manage App Shortcut.Enter a value under Startmenu Directory and Destktop Directory. Click OK.And here is the Desktop folder. Here is the Start Menu folder. If you want to supress messages that applications have been removed in the event you do remove applications or resources users are subscribed to you can create a registry value. Create a REG_SZ entry with the name DontWarnOfRemovedResources and a value of true. Create this entry in:
HKLMSoftwareCitrixDazzle – 32bit machines.
HKLMSoftwareWOW6432NodeCitrixDazzle – 64bit machines.
Some older versions of Receiver do not seem to “recreate” a shortcut if a user deletes it. Newer versions do seem to do this. If you are having trouble getting a deleted shortcut to reappear you could try the following:
- Open CMD on the affected machine and change directory to
- C:Program FilesCitrixICA ClientSelfServicePlugin (32bit machines)
- C:Program Files (x86)CitrixICA ClientSelfServicePlugin (64bit machines)
- Run command CleanUp.exe -cleanUser
Setting shortcuts to delete on Receiver exit or logoff
If you have machines shared between users under a single generic user account, you might find it useful to delete Self Service generated shortcuts when a user logs off Citrix Receiver or exits the application.
Configure Citrix Receiver To Manually Add Http Stores Free
You can configure this behaviour either by creating the below strings under the HKCU hive for all your users or else have Group Policy do it instead. It is possible to create the below strings under HKLM on each machine, but I’ve found it more consistent to do so under HKCU. Either way, make sure to test the behaviour and confirm it works before deploying out.
To set shortcuts to delete on Receiver logoff and/or exit create string RemoveAppsOnExit and/or RemoveAppsOnLogoff under HKCUSoftwareCitrixDazzle.
Configure Citrix Receiver To Manually Add Http Stores To Search
To manage the behaviour using Group Policy enable the Manage App Shortcut policy, part of the Receiver ADMX files that can be downloaded from Citrix.
Additional Notes
Configure Citrix Receiver To Manually Add Http Stores List
If you have difficulty getting applications to show on the desktop or start menu be sure to read this https://www.jgspiers.com/citrix-self-service-applications-not-appearing-start-menu-desktop/